
GitHub has actually turned its personal SSH secret for GitHub.com after the trick was was unintentionally released in a public GitHub repository.
The software application advancement and variation control service states, the personal RSA secret was just “quickly” exposed, however that it acted out of “an abundance of care.”
Uncertain window of direct exposure
In a concise post released today, GitHub acknowledged finding today that the RSA SSH personal secret for GitHub.com had actually been ephemerally exposed in a public GitHub repository.
” We instantly acted to include the direct exposure and started examining to comprehend the source and effect,” composes Mike Hanley, GitHub’s Chief Gatekeeper and SVP of Engineering.
” We have actually now finished the crucial replacement, and users will see the modification propagate over the next half an hour. Some users might have discovered that the brand-new secret was quickly present starting around 02:30 UTC throughout preparations for this modification.”
The timing of the discovery is fascinating– simply weeks after GitHub presented tricks scanning for all public repos.
GitHub.com’s newest public crucial finger prints are revealed listed below. These can be utilized to confirm that your SSH connection to GitHub’s servers is undoubtedly protected.
As some might observe, just GitHub.com’s RSA SSH secret has actually been affected and changed. No modification is needed for ECDSA or Ed25519 users.
SHA256: uNiVztksCsDhcc0u9e8BujQXVUpKZIDTMczCvj3tD2s ( RSA)
SHA256: br9IjFspm1vxR3iA35FWE +4 VTyz1hYVLIE2t1/CeyWQ ( DSA – deprecated)
SHA256: p2QAMXNIC1TJYWeIOttrVc98/R1BUFWu3/LiyKgUfQM ( ECDSA)
SHA256:+ DiY3wvvV6TuJJhbpZisF/zLDA0zPMSvHdkr4UvCOqU ( Ed25519)
” Please keep in mind that this concern was not the outcome of a compromise of any GitHub systems or client info,” states GitHub.
” Rather, the direct exposure was the outcome of what our company believe to be an unintentional publishing of personal info.”
The post, nevertheless, does not address when precisely was the crucial exposed, and for for how long, making the timeline of direct exposure a bit dirty. Such timestamps can normally be determined from security logs– ought to these be offered, and Git devote history.
GitHub additional states it has ” no factor to think” that the exposed secret was mistreated, and turned the crucial ” out of an abundance of care.”
However, turning a personal secret once it has actually been dripped, no matter how ‘quickly,’ is any method a required action to secure users from enemies who might possibly impersonate your server, or be all ears on a user’s connection.
The exposed RSA type in concern does not give access to GitHub’s facilities or client information, Hanley has actually clarified.
” This modification just affects Git operations over SSH utilizing RSA. Web traffic to GitHub.com and HTTPS Git operations are not impacted.”
Double-check that finger print
Although GitHub has actually altered the personal SSH secrets, several docs and software application tasks consisting of those by GitHub, continue to utilize the SSH finger print of its now-revoked secret:
SHA256: nThbg6kXUpJWGl7E1IGOCspRomTxdCARLviKw6E5SY8
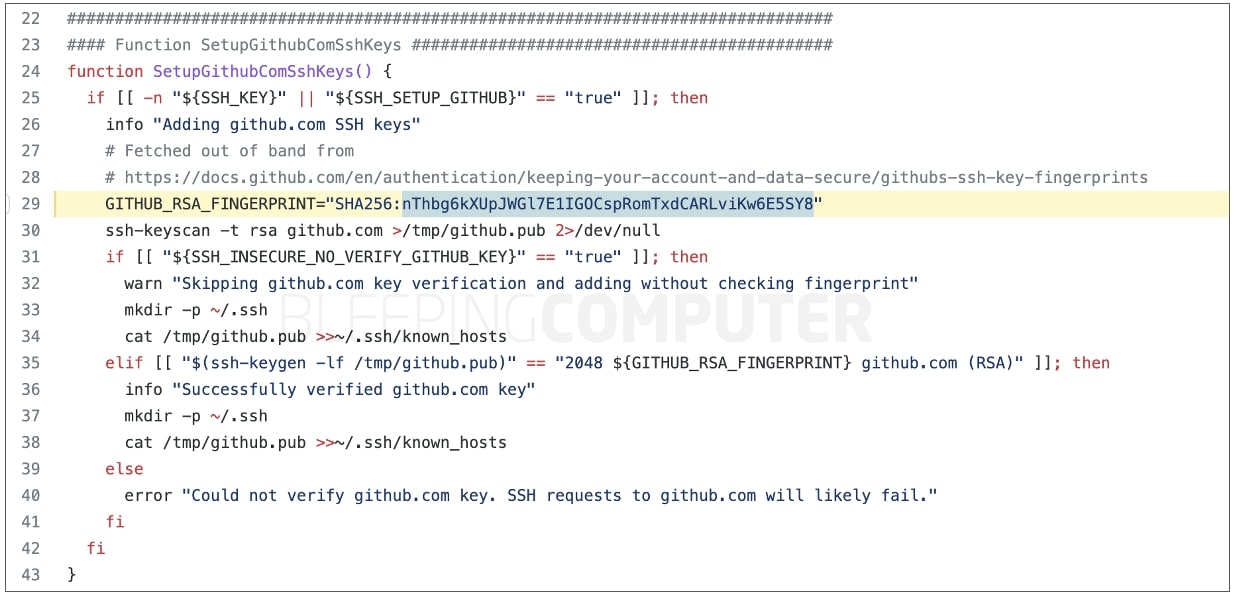
As such, users ought to upgrade their ~/. ssh/known _ hosts file with GitHub’s brand-new crucial finger print, otherwise they might see security cautions when making SSH connections. When getting such cautions, users ought to guarantee the finger print seen on their screen matches the one for GitHub.com’s newest secret.
Since in 2015, GitHub’s approximately date SSH host secrets are likewise released to its API metadata endpoint